Trivy is an open-source vulnerability scanner designed to identify security issues in container images and filesystems. It was developed specifically for use with container technologies like Docker, Kubernetes, and others. Trivy is widely used in the DevSecOps workflow to automate vulnerability assessments and ensure the security of containerized applications.
Trivy scans container images and file systems for known vulnerabilities by comparing the package versions installed within them against a comprehensive vulnerability database. It leverages multiple vulnerability databases, including the National Vulnerability Database (NVD), Red Hat Security Data, and various language-specific databases.
The scanner can detect various types of vulnerabilities, such as operating system package vulnerabilities, library vulnerabilities, insecure configurations, and even issues related to the base images used in containerization. Trivy provides a report that highlights the identified vulnerabilities, including their severity levels and references to relevant advisories.
By integrating Trivy into your development pipeline or continuous integration/continuous deployment (CI/CD) process, you can automatically assess the security of your container images at different stages, such as during the build process or before deployment. This helps identify vulnerabilities early in the development cycle, allowing developers to address them promptly and improve the overall security posture of their applications.
It's worth noting that Trivy is a command-line tool, but there are also integrations available for various popular container registries and CI/CD platforms, making it easier to incorporate Trivy into existing workflows.
To use Trivy, you can follow these general steps:
Installation:
- Trivy can be installed on various platforms, including Linux, macOS, and Windows. Refer to the Trivy documentation for the latest installation instructions: Installation - Trivy (aquasecurity.github.io)
Scanning Container Images:
Run Trivy against a container image by executing the following command:
trivy image <IMAGE_NAME> # or trivy i <IMAGE_NAME>Replace
<IMAGE_NAME>with the name or URL of the container image you want to scan. Trivy will automatically download the necessary vulnerability database.Scan a container image from a tar archive
trivy image --input <TAR_FILE_PATH>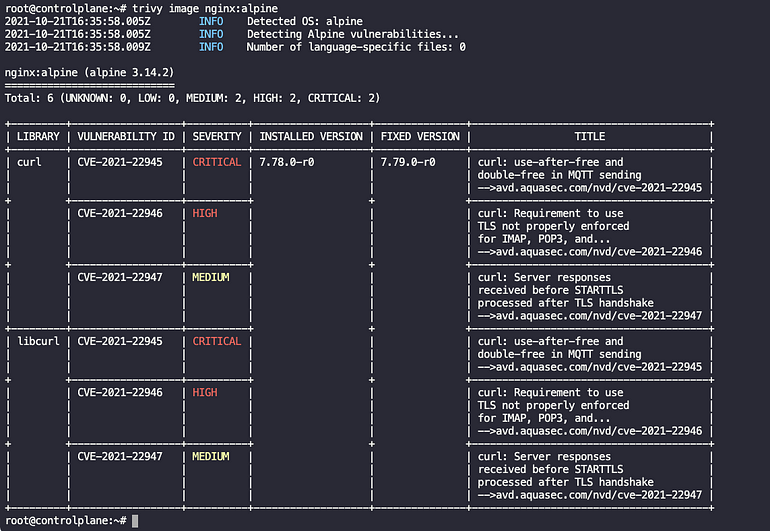
As you can see, the below nginx image(nginx:alpine) has a total of 6 vulnerabilities with Severity of (Critical, Medium, and High).
If you only want to see vulnerability with Severity of type Critical
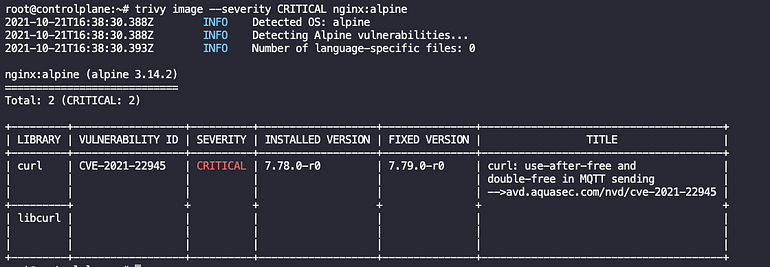
Scanning Filesystems or Directories:
You can also scan local filesystems or directories by running the following command:
trivy fs --scanners vuln,secret,config <DIRECTORY_PATH>It's also possible to scan a single file.
trivy fs <FILE_PATH>Replace
<DIRECTORY_PATH>with the path to the directory or filesystem you want to scan.
Scanning git repository
trivy repo <REPO_URL>
# specific branch
trivy repo --branch <BRANCH_NAME> <REPO_URL>
# scan specific commit
trivy repo --commit <COMMIT_ID> <REPO_URL>
# scan specific version if have
trivy repo --tag <VERSION> <REPO_URL>
# scan private repo
export GITHUB_TOKEN=<TOKEN>
trivy repo <PVT_REPO_URL>
trivy repo --scanners vuln,secret,config <REPO_URL>
Advanced Options:
Trivy provides additional options to customize the scan process. Some commonly used options include:
--severity: Filter vulnerabilities by severity (e.g., CRITICAL, HIGH, MEDIUM, LOW).--ignore-unfixed: Ignore vulnerabilities without a fixed version available.--format: Specify the output format (e.g., table, json, template).
Refer to the Trivy documentation for a complete list of available options: Overview - Trivy (aquasecurity.github.io)
Discover security misconfigurations
In the belove manifest, we have purposefully set the privileged attribute within the securityContext to true. Unfortunately, that is also security malpractice and should be avoided.
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx
spec:
selector:
matchLabels:
app: nginx
replicas: 1
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx:1.14.2
ports:
- containerPort: 80
securityContext:
privileged: true
Now, let’s try to run the scan and see what Trivy tells us. To do so, use the following command:
trivy config <config_dir>

And as we see, we get the listed set of vulnerabilities within the configuration. I need to point out that it has been detected that we have the root user within the Dockerfile, which is not a security best practice. We are also trying to run the Kubernetes deployment in privileged mode, and it has detected that.
Conclusion
Trivy works quite well as a comprehensive static security analysis tool for container images and related configuration, and it gels well with your CI pipelines. If implemented effectively, it can greatly enhance your security posture.